1. Introduction.
Scanning is the second phase of performing ethical hacking. After collecting data in reconnaissance we will move on to the phase of scanning. In this phase we do scan for the vulnerabilities (weaknesses) in the system through which we can enter into it. So in this blog, I’ll share how I performed scanning using kali Linux tools in real time.
2. What is Scanning?
Scanning means to find out if system or network in vulnerable. It involves finding out open ports, services or vulnerabilities.
3. Types of Scanning.
- Port scanning.
- Network scanning
- Vulnerability scanning
4. Tools I use in scanning:
In scanning there is a tool which is most widely used is named as Nmap to perform scan on networks, to find Vulnerability & for ports scanning. Also there are few tools which used for scanning phase to perform like
- Zaproxy
- Zenmap
- Nikto
- hping3
- Netdiscover
- Nmap
Yes few tools also used for Recon as well like nmap but main purpose is to do scanning.
5. Step by Step Practical Scanning with different tools:
As a cyber security student I performed practical with nmap in kali and I used tested website to scan.
“testphp.vulnweb.com”
Nmap is a powerfull network scanning tool, to ensure web app vulnerability
I am targeting a safe & legal website by Acunetix.
– Nmap
- What this tool does?
I tried tool called as nmap, which is used for scanning phase of ethical hacking. It can discover the live hosts, open ports services and OS infos.
- What commands I use?
The commands I used is mentioned below also I attached the screen shots of my practice lab.
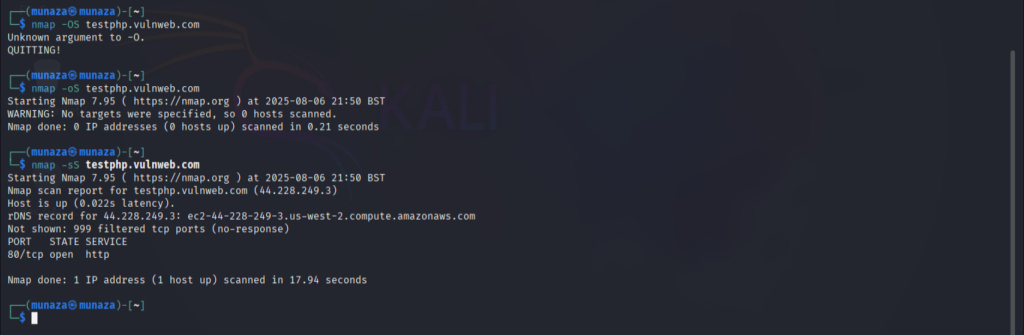
nmap testphp.vulnweb.com
nmap -A testphp.vulnweb.com
nmap -p 80,443 testphp.vulnweb.com
nmap –sS –oS –sV testphp.vulnweb.com
-A is used for aggressive scan so use it wisely with care, while –os is for findind which operating sytem is used by target. –SV is used to know service version, it can be vulnerable if target is using old version. Perform all scans one by one, if you do all at same time that will takes alot of time.
– What information is revealed?
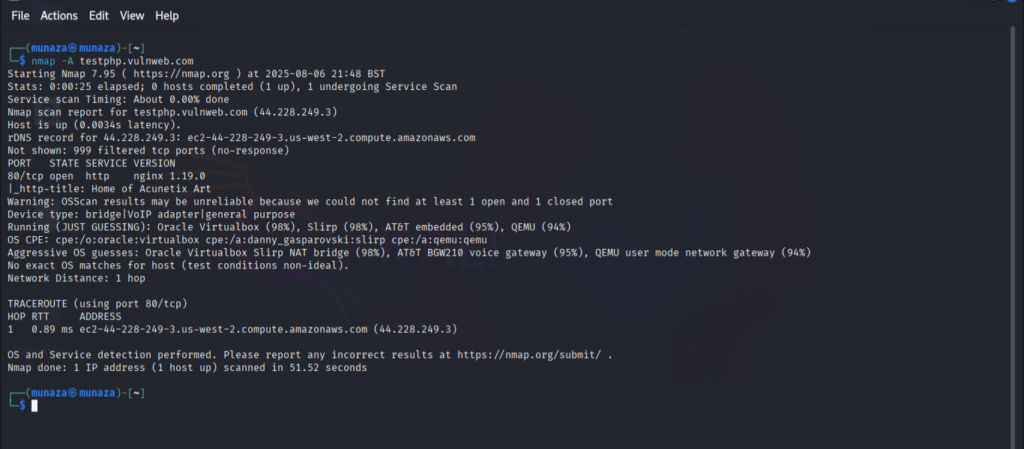
I attached the screenshot of the end result which shows the revealed information’s after using tool and correct command in kali Linux. It will reveal the OS, Service version & open ports etc.
Result:
- Host is up: 44.228.249.3
- Open Port: 80/tcp (HTTP)
- Service: nginx 1.19.0
- Page Title: Home of Acunetix Art
- OS Detection Guess: Oracle VirtualBox / QEMU / AT&T embedded
- Traceroute: 1 hop (Amazon EC2 server)
- 999 ports filtered (no response)
They are running services and we got version so it can be vulnerable because its old version and exploit is also available. Screen shots are attached here below.
-Zaproxy
- What this tool does?
I tried tool called as zaproxy, which is used for scanning phase of ethical hacking. It is GUI based web scan tool, which find the vulnerabilities and then rank them accordingly.
- What commands I use?
It is GUI (graphic user interface) tool so screenshot are attached. It’s very simple to scan with zaproxy, just enter the target url and then press start scan.
– What information is revealed?
I attached the screenshot of the end results. This tool shows the vulnerabilities in medium, low and high rank.
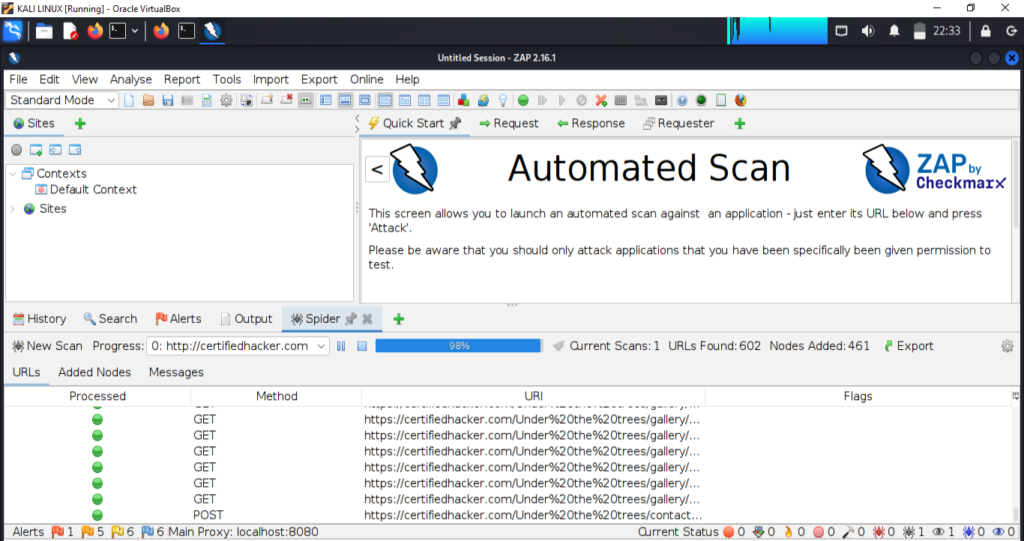
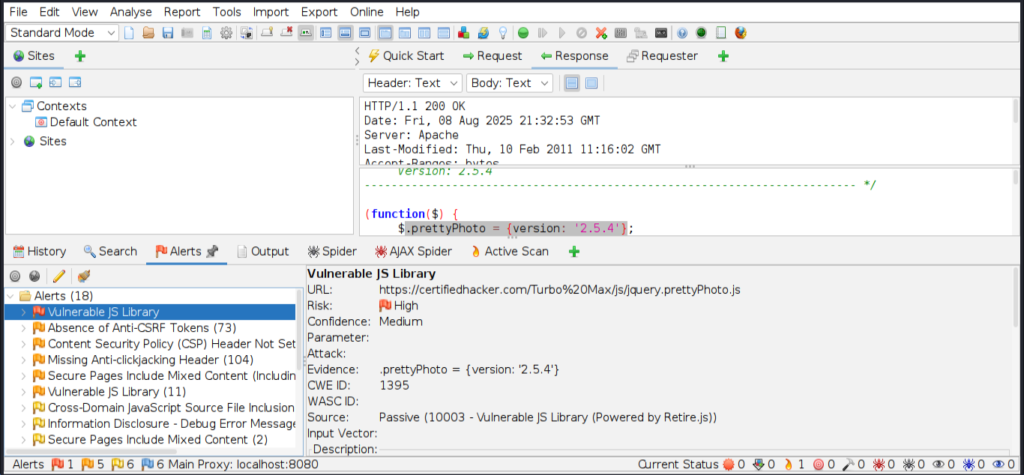
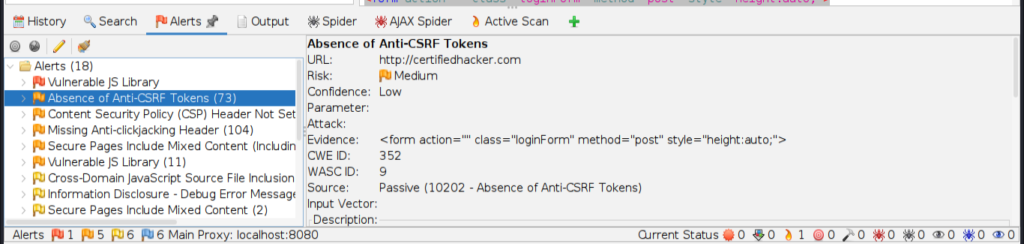
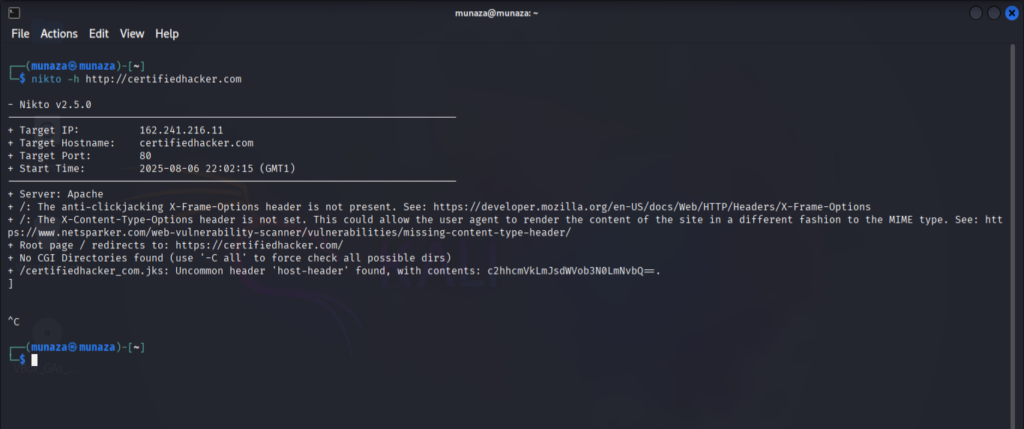
– Nikto
- What this tool does?
I tried tool called as nikto, which is web server Vulnerability scanner. Used to scan like outdated services, software’s or misconfiguration.
- What commands I use?
It is tool for scanning Vulnerability available in Kali Linux, command I use is;
“nikto -h certifiedhacker.com”
– What information is revealed?
I attached the screenshot of the end results. This tool shows the outdated software, potential vulnerability & server info.
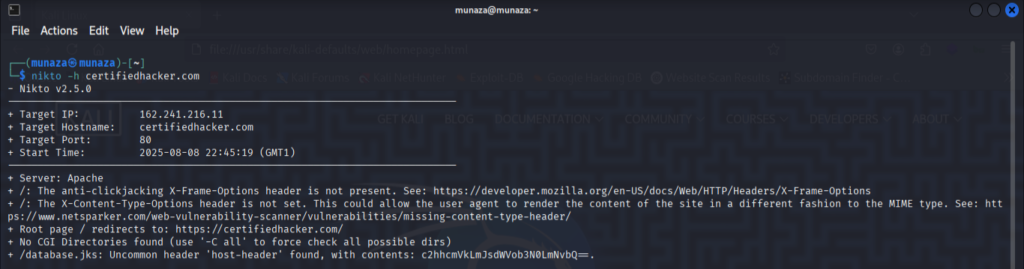
– Netdiscover
- What this tool does?
I tried tool called as netdiscover, it is used to find live host on local network.
- What commands I use?
It is tool for scanning Vulnerability available in Kali Linux, command I use is;
“sudo netdiscover -r 162.241.216.11/24”
– What information is revealed?
I attached the screenshot of the end results. This tool shows the IP, MAC Address and vendor details.
6. Learnings:
After this practical I learned;
How to scan networks or services to identify open ports before performing attack on target. I learned how to use nmap different flags for performing different scans like –Os for operating systems etc. And I learned the importance of scanning before the exploitation phase.
7. Conclusions:
The scanning phase practice helped me to fulfill the gap between theory and practical knowledge. I’m sharing my journey to becoming a cyber-security professional step by step through blog posts, hands-on labs, and GitHub projects. Here is my github project link you can check it or you can also follow me on my other social media profiles. https://github.com/munazajamil/Kali-Recon-Practice. So if you want to start learning ethical hacking start with free resources available on YouTube and read books. You can go for short term diploma or you can also enroll in full time degree as well. Just start Learning and share you journey with me. If you found this guide useful. Keep an eye out for additional cyber security tutorials for beginners! Stay tuned with my blog for additional real life cyber security walkthroughs. Just check out the cyber security roadmap for beginners. https://munazajameel.site/cybersecurity-roadmap-2025-beginners/. OR you can check out my YouTube channel for better content. https://www.youtube.com/@itzmunazah
See you next time!