7 Phases of a Cyberattack Explained!
Introduction to Cyber Kill Chain:
Cyber Kill Chain means the phases of attack performed in ethical hacking. It is like a kind of hacker’s playbook. Cyber Kill Chain is a structured series of steps that attackers follow to breach systems and carry out their malicious missions. These steps help organizations to detect and stop the threats early. Cyber Kill Chain was originally developed by the defense contractor Lockheed Martin to understand how real-world cyber-attacks happen and how to defend against them.
These are mainly 7 Phases of cyber kill chain.
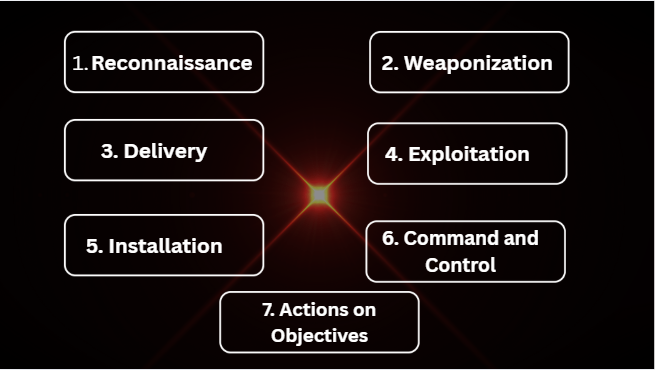
1. Reconnaissance:
The first phase of Cyber Kill Chain is known as Reconnaissance. Where cyber attackers act like a digital investigator. In addition, their goal is to gather as much information as possible about the target before launching the actual attack.
There are two types of Reconnaissance.
- Passive Reconnaissance
- Active Reconnaissance
In passive reconnaissance, attackers gather publicly available information without interacting directly with the target. For example, checking websites, social media handles, and using tools like OSINT, (Open Source Intelligence).
In active reconnaissance, attackers directly engage with the target’s system, such as scanning the network to find open ports or vulnerabilities. It’s like trying to open a door knob without actually entering the house door key. Hackers may also use social engineering during this phase to trick the people into giving away system information, like passwords, OTPs, through phishing emails, or by playing with their psychology. Some even go to the extent of a dumpster. Reconnaissance is basically about gathering clues before attack launch by attacker.
2. Weaponization:
The second phase of Cyber Kill Chain is known as Weaponization means building the cyber weapon. In this stage, attackers create a malicious payload based on the information they gathered. This could be a virus, ransomware, or often combined with a normal looking file like with a PDF or Word document. The goal is to turn their plan into a working digital weapon that can harm the target system when delivered and activated. In simple words, weaponization is this phase where attacker creates a weapon to attack on the target.
3. Delivery:
The third phase of Cyber Kill Chain is known as Delivery. Delivery means sending the malware to the target. Once the cyber weapon is ready, it needs to be delivered to the target. Delivery is all about finding a way to send the malware without knowledge of target. Some common delivery methods include;
- Phishing email means with a fake message and infected attachment. Phishing emails contain fake links.
- Drive-by-downloads means by just visiting a compromised website triggers a malware download.
- Infected USB drive means left that USB in the public place in hope someone will plug that into their computer.
- Watering hole attacks mean where hackers infect the website that the target often visits.
This phase is like a secret drop-off operation to deliver the weapon without being noticed. In simple, delivery means the delivery of that prepared weapon to the target.
4. Exploitation:
The fourth phase of Cyber Kill Chain is known as Exploitation. It means taking advantage of weaknesses of target’s system. After delivery the next phase is where the malware gets triggered and take advantage of system weakness or vulnerabilities. The main goal here is to gain unauthorized access of target system. For example, if there is a flaw in software program that was not updated or password protected, attackers can exploit it to break in. This stage reminds us why it’s important to regularly patch and update the software so these vulnerabilities are closed before the attackers can use them. In simple, take advantage of weakness and enter into system of target.
5. Installation:
The fifth phase of cyber kill chain is known as Installation. It means creating a foothold inside the system.
Now that the system is compromised by using exploitation of any vulnerability, attackers need to ensure that they stay inside.
In Installation phase, they install the malware or open the backdoors that let them control the system later. It’s also known as Advanced Persistent Attack, means to maintain a system control for a long time.
For that they add the persistence mechanism so that even if the system restarts or tries to clean up, the malware stays. It’s like a hidden software looks like book icon into a system and hiding inside but in actual it’s not real book, so the target will thought it’s just a normal book. Leaving behind a secret door or a secret key to open back whenever they want. Some examples include remote access tools, hidden software, or files disguised as normal programs.
6. Command & Control (C2):
The sixth phase of Cyber Kill Chain is known as Command and Control. It means a remote communication. After setting up inside the system, attackers want to control it remotely. The Command and Control phase is where they set up convert communication channels to send instructions to the compromised device. This can involve;
- Botnets, means where many infected computers are controlled together.
- RDP exploitation, Remote Desktop Protocols, means where the attackers take control of system remotely.
- DGA, Domain Generation Algorithm, means to frequently change command server address and avoid detection.
- Hidden Communication Channels, means where attackers hide malicious messages in normal internet traffic.
This phase allows attackers to steer the attack from anywhere. In simple, to perform attack from anywhere in the world and have complete control of it.
7. Actions on Object:
The seventh and the last phase of cyber kill chain are known as actions on object. It is the final goal of performing attack. Finally the attacker executes their real purpose, so this could be;
- Data exfiltration, means stealing sensitive data like password, credit card details, or confidential files.
- Disrupting services, means launching attack like DDoS to make websites or servers crash and down.
- System destruction means corrupting or destroying the files, disabling system or damaging equipment.
- Ransom ware attack means locking file of target and demanding payment to unlock them.
This is the phase where real damage happens, whether it’s theft, destruction, or financial loss.
Conclusion:
The Cyber-Kill chain provides us with a step-by-step understanding of how cyberattacks occur. We have an opportunity to identify, halt, or avoid the attack at each stage. Defenders can prevent significant system damage if they can detect and stop the attack early, for example, during the reconnaissance or delivery phase.
So if you want to start learning ethical hacking start with free resources available on YouTube and read books. You can go short term diploma or you can also enroll in full time degree as well. Just start Learning and share you journey with me. If you found this guide useful. keep an eye out for additional cybersecurity tutorials for beginners! Stay tuned with my blog for additional real life cyber security walkthroughs.
Just check out the cyber security roadmap for beginners. https://munazajameel.site/cybersecurity-roadmap-2025-beginners/. OR you can check out my youtube channal for better content. https://www.youtube.com/@itzmunazah
See you next time!