My Practical approach for Reconnaissance in Ethical hacking. Tools, Commands & Practical Guide (2025)
Introduction:
The word Reconnaissance means “gather or collect information” so when we want to target any system ethically. We will collect their basic infos which are available publically on internet. There are two ways of that information collection.
- Active Reconnaissance
- Passive Reconnaissance
Types of Reconnaissance:
There are mainly two type of recon. We can perform and use these both types to gather target’s all kind of data which would be helpful for future attacks.
What is Passive Reconnaissance?
The “passive recon” is the type when we collect data without interacting with the target. Like target didn’t know that we are gathering their data. All we do is just collect the data available on internet using techniques like google dorking or by using tools in kali. The tools today I use to perform this in kali are named as, whois, host, Recon-ng, shodan, Maltego, nslookup, google dorking, TheHarvester, Spiderfoot & subfinder etc. I will discuss in details later in blog what I did practically.
What is Active Reconnaissance?
The “active recon” is the type when we directly interact with the target by using different tools like nmap. It’s really popular tool of kali that will perform a full scan on website and target will know that someone is trying to bypass. The tools today I use to perform this in kali are named as, Nmap, nikto, whatweb, wapiti, dirb/gobuster, metasploit, Hping3 & netcat etc.
Tools & commands I use for Passive Recon:
- “Whois”
. What this tool does?
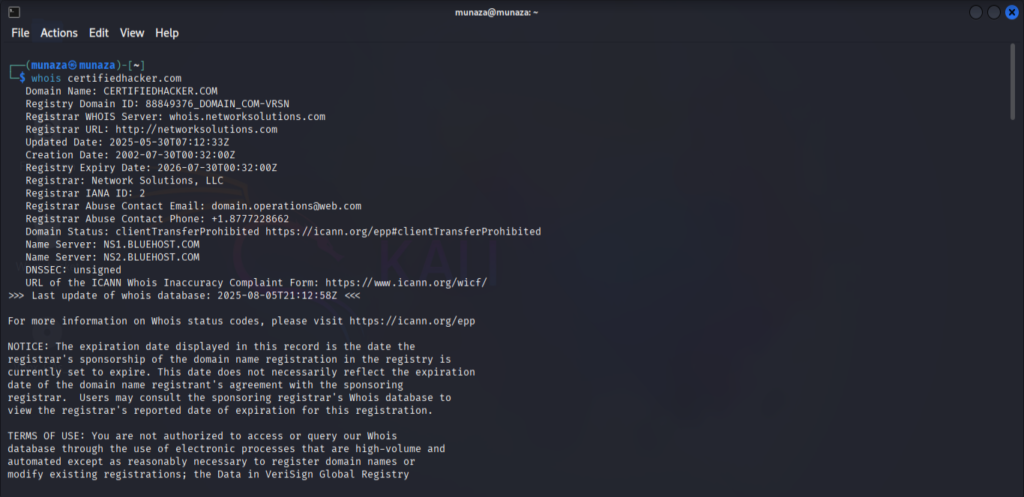
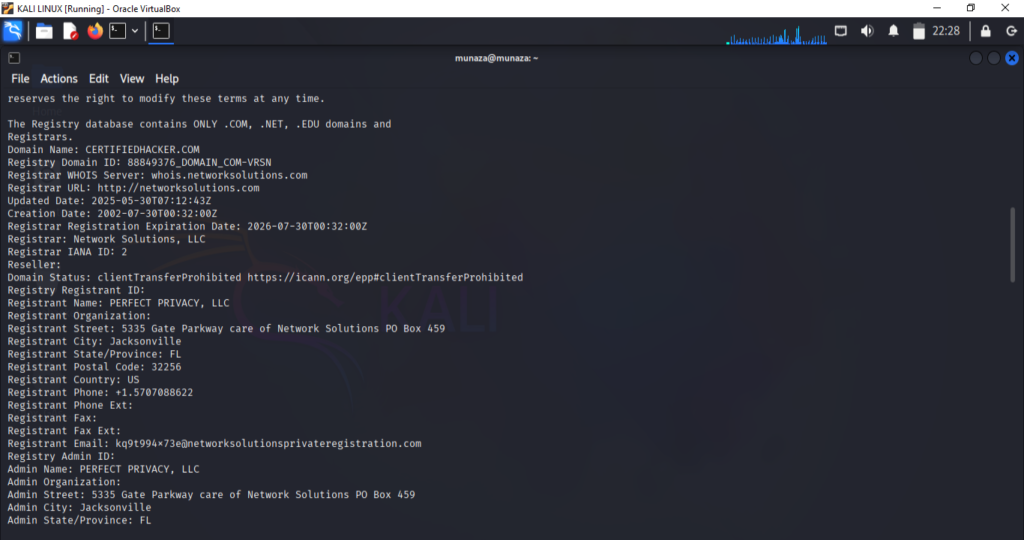
“whois” this tool is super easy to use in kali. It is passive recon command line tool that will find for us a public info about the target. It’s pre-installed in new version of kali. So I just type whois and then paste my targets’s url.
The exact command I run?
Whois certifiedhacker.com
I run this command to find information about my target. As I am testing so there are few websites which is made for testing practice. So I use one of that otherwise performing recon about anyone is illegal and strongly prohibited. So always take permission to perform ethically.
- What output I got?
So when I perform that command I got results like who own’s website, when its created and when it updated. I attached the screenshot from my kali Linux screen of real time scenario.
- What information it revealed?
I attached the screenshot of the end result which shows the revealed information’s after using tool and correct command in kali Linux.
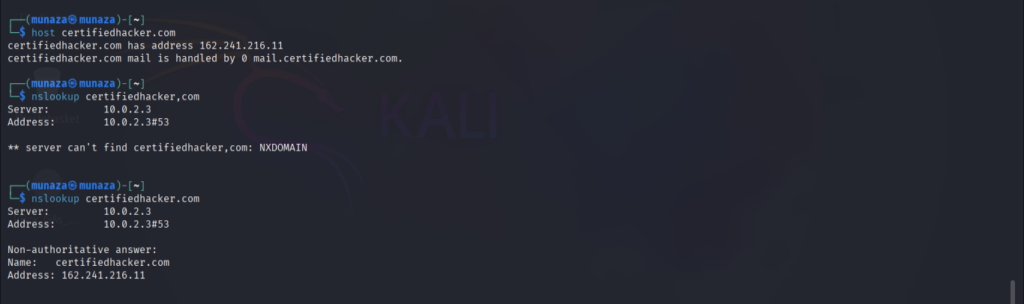
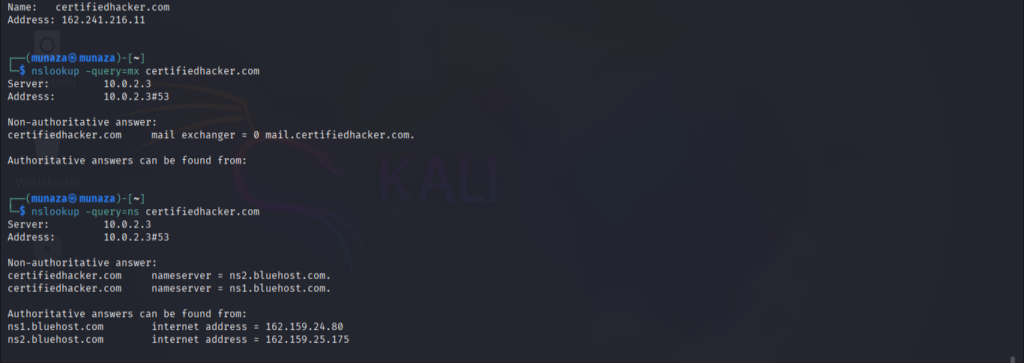
2. “Host & nslookup”
- What this tool does?
I tried both tools and these tools used widely for passive recon in ethical hacking. Nslookup tool is used to find DNS records of target such as IP Address, server name(ns) , mail server(mx). While the host tool also do same work like nslookup. It’s like a backup tool of nslookup.
What commands I use?
The commands I used is mentioned below also I attached the screen shots of my practice lab. So you can see what exactly it looks like as end result.
host certifiedhacker.com
or for nslookup I use,
nslookup certifiedhacker.com
nslookup -query=mx certifiedhacker.com
nslookup -query=ns certifiedhacker.com
- What information is revealed?
I attached the screenshot of the end result which shows the revealed information’s after using tool and correct command in kali Linux.
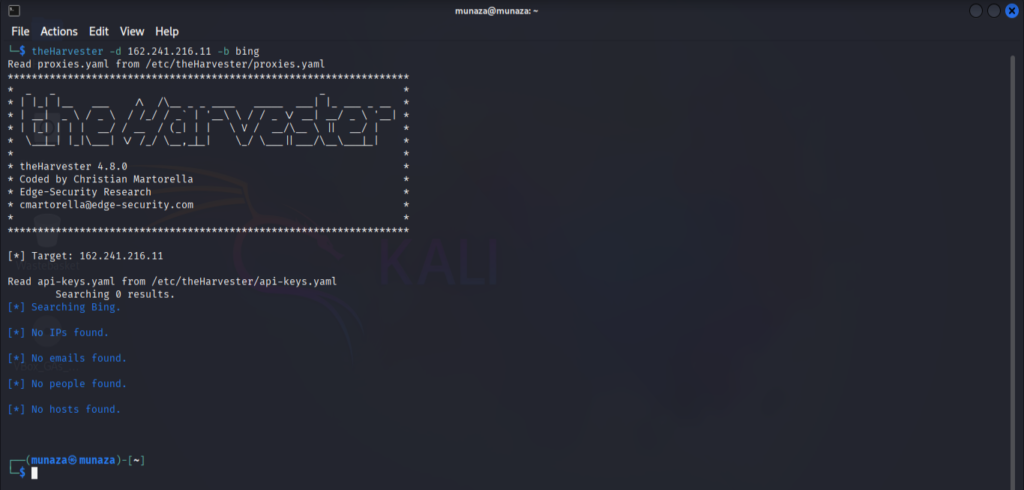
3. “theHarvester”
- What this tool does?
I tried tool called as theHarvester, which is used for passive recon in ethical hacking. theHarvester tool is OSINT tool, used to find emails, subdomains, IPs & hostnames of the target. But for that we also had to mention like from where we want to collect data like from google, linkdin or bing etc.
- What commands I use?
The commands I used is mentioned below also I attached the screen shots of my practice lab. So you can see what exactly it looks like as end result.
theharvester -d certifiedhacker.com -b bing/google
- What information is revealed?
I attached the screenshot of the end result which shows the revealed information’s after using tool and correct command in kali Linux. Even though I didn’t find as such results because of public target but you can see how it looks like when it runs. I attached the screen shot of my machine.
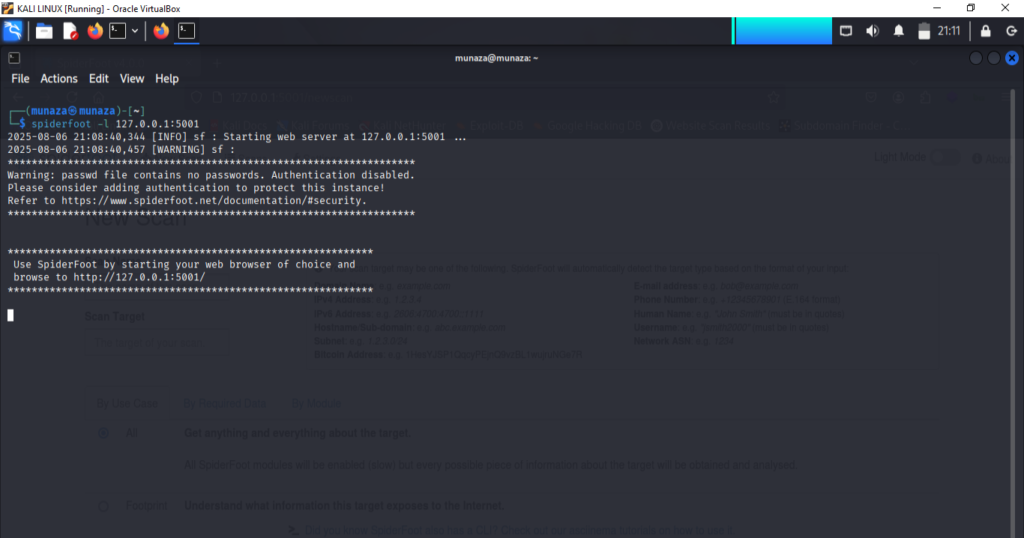
4. “Spiderfoot”
- What this tool does?
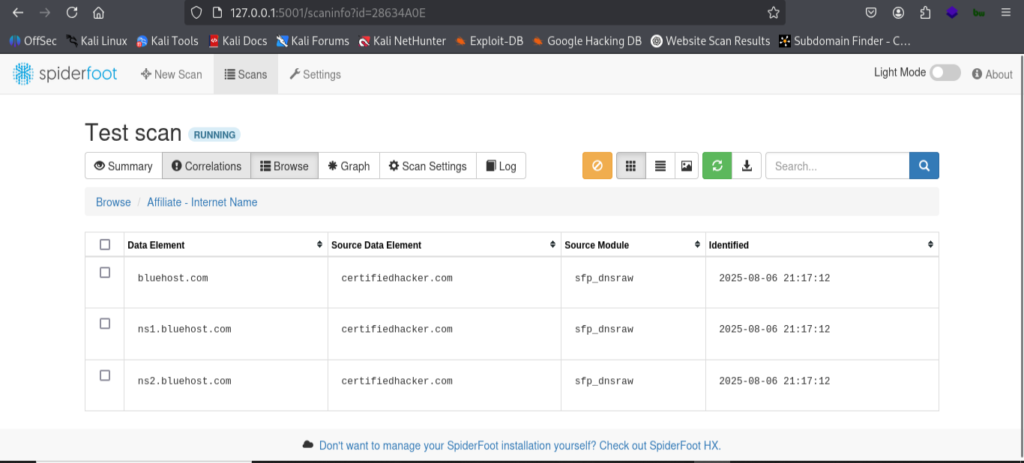
I tried tool called as spiderfoot, which is used for passive recon but also do sometimes active recon in ethical hacking. It is OSINT tool and il collect the information of target from overall 100+ sources. It is basically opposite of theHarvester tool. As in harvester we have to specify the source name but in spiderfoot it will crawl all over the internet and find publically available data.
- What commands I use?
The commands I used is mentioned below also I attached the screen shots of my practice lab. So you can see what exactly it looks like as end result. Like in spider foot I mentioned here the local host IP and the unknown ports which is not already running in my system.
spiderfoot -l 127.0.0.1:5001
This will open the GUI of tool, paste it to browser. Then you can add domain name, IP and start the scan.
Spiderfoot –help
You can run this command to learn all about the tool.
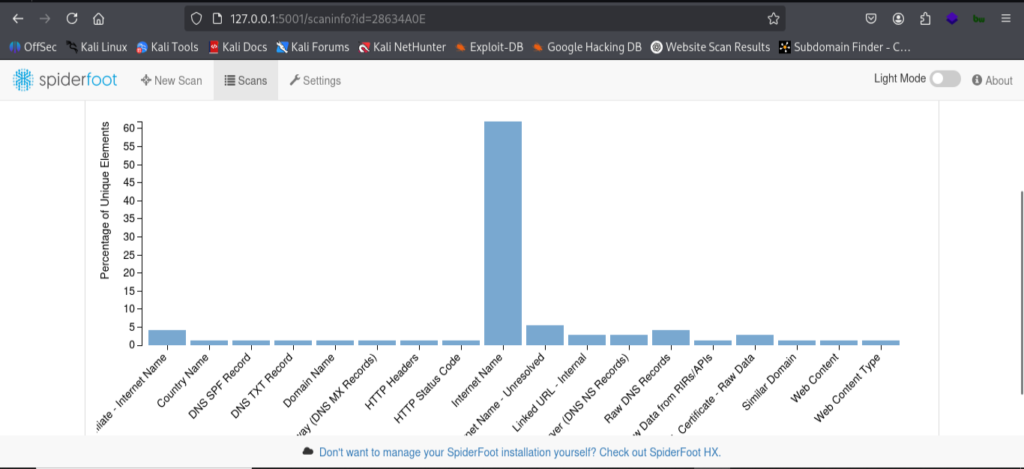
- What information is revealed?
I attached the screenshot of the end result which shows the revealed information’s after using tool and correct command in kali Linux. It will collect the IP Address, subdomains, emails, DNS info, phone numbers, WHOIS info, breach data and much more. It will show in graphical manner.
Tools & commands I use for Active Recon:
- “Nmap”
. What this tool does?
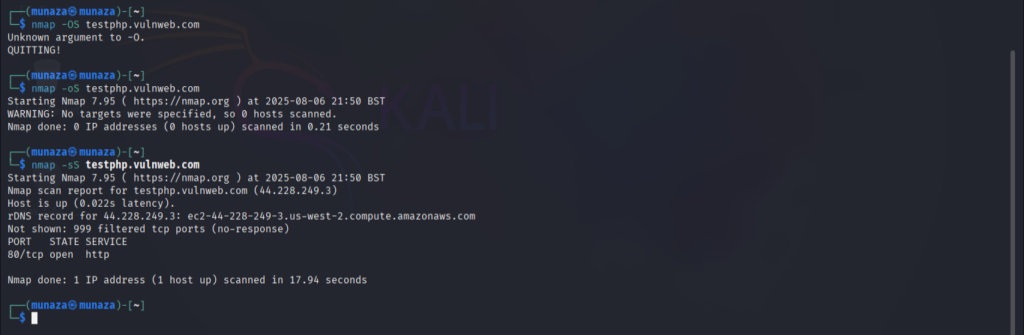
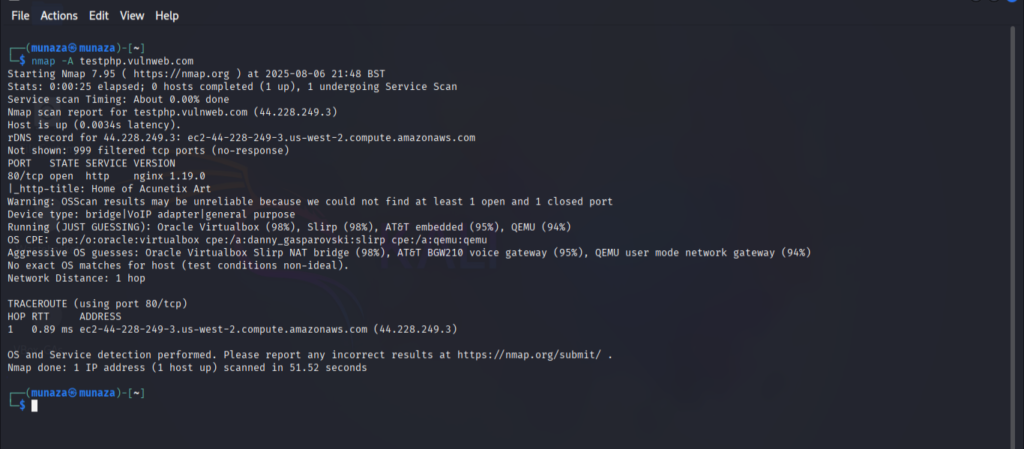
I tried tool called as nmap, which is used for active recon but also mainly used in scanning phase of ethical hacking. It can discover the live hosts, open ports services and OS infos.
- What commands I use?
The commands I used is mentioned below also I attached the screen shots of my practice lab.
nmap certifiedhacker.com
nmap -A certifiedhacker.com
nmap -p 80,443 certifiedhacker.com
nmap –sS –oS –sV certifiedhacker.com
-A is used for aggressive scan so use it wisely with care, while –os is for findind which operating sytem is used by target. –SV is used to know service version, it can be vulnerable if target is using old version.
– What information is revealed?
I attached the screenshot of the end result which shows the revealed information’s after using tool and correct command in kali Linux. It will reveal the OS, Service version & open ports etc.
2. Nikto
- What this tool does?
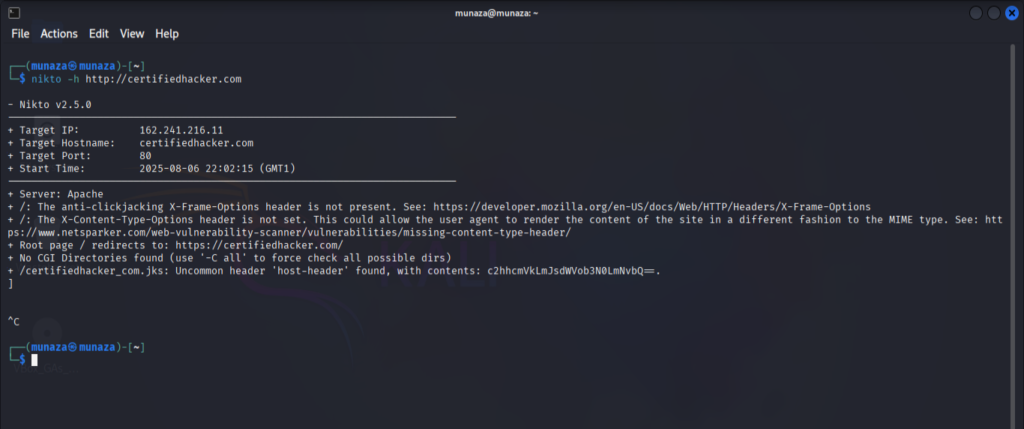
I tried tool called as Nikto, which is used for active recon but also mainly used in scanning phase of ethical hacking. It can scan the web server for vulnarabilities.
- What commands I use?
The commands I used is mentioned below also I attached the screen shots of my practice lab.
nikto -h certifiedhacker.com
– What information is revealed?
I attached the screenshot of the end result which shows the revealed the outdated server software, dangerous files & scripts, Misconfigurations.
2. WhatWeb
- What this tool does?
I tried tool called as WhatWeb, which is used to find which technology at backend organixation or company used. For this purpose we can also use extensions like “wappa;yzer” & “builtwith” .
- What commands I use?
The commands I used is mentioned below also I attached the screen shots of my practice lab.
whatweb certifiedhacker.com
– What information is revealed?
I attached the screenshot of the end result which shows the revealed the backend technology like wordpress, css, java etc. Also it reveal the analytics, java libraries, & CSMs.
3. Wapiti
- What this tool does?
I tried tool called as Wapiti, which is used to find web app Vulnerability.
- What commands I use?
The commands I used is mentioned below also I attached the screen shots of my practice lab.
Wapiti –u certifiedhacker.com
– What information is revealed?
I attached the screenshot of the end result which shows the revealed the XSS, SQL injection, file disclosure, & command execution flaws.
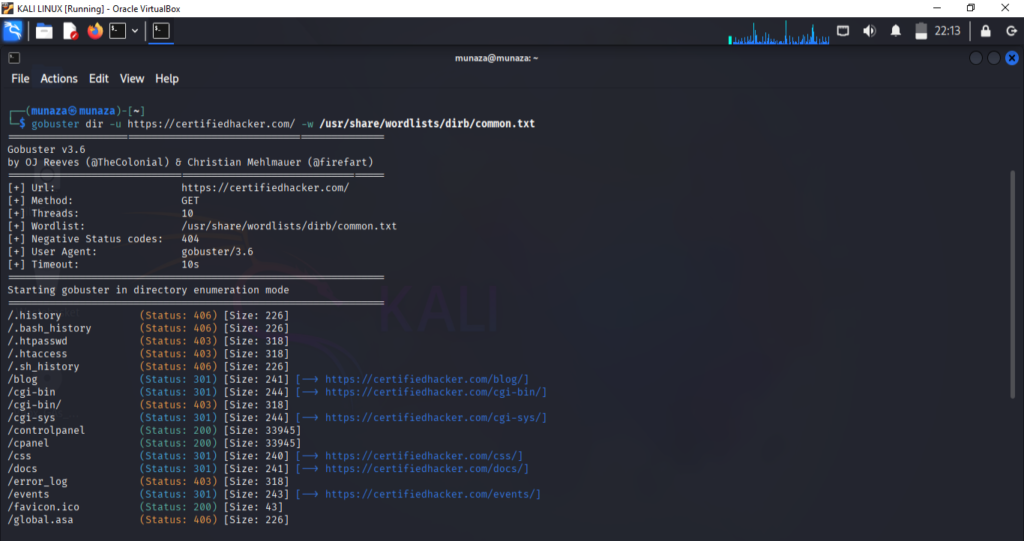
4. Dirb/gobuster
- What this tool does?
I tried tool called as dirb/gobuster which is used to find hidden directories & in file brute forcing.
- What commands I use?
The commands I used is mentioned below also I attached the screen shots of my practice lab.
dirb certifiedhacker.com
gobuster dir –u certifiedhacker.com –w /usr/share/wordlists/dirb/common.txt
Here –u used for url while –w is used for wordlist directory. We will define a word list from where it will perform a brute force.
– What information is revealed?
I attached the screenshot of the end result which shows the revealed the hidden directories & files, backup/config files, admin panel details.
Learnings:
I performed both active and passive recon in my kali machine on publically available website in ethical way. I did all just for practice and my knowledge. This content is only for educational purpose and nothing illegal performed neither shown nor shared in the blog. I learned how we can collect the valuable data by using passive recon without even touching target. On the other hand through active recon I learned we can find hidden directories, or open ports to enter into the system.
In ethical hacking, reconnaissance is the first and also important phase. It provides the foundations for the later phases like scanning, exploitation, gain access or removal of tracks. Do spend time in good recon because it will save your time and also increase the chances of performing successful attack.
Conclusions:
The recon phase practice helped me to fulfill the gap between theory and practical knowledge. I’m sharing my journey to becoming a cyber-security professional step by step — through blog posts, hands-on labs, and GitHub projects. Here is my github project link you can check it or you can also follow me on my other social media profiles. https://github.com/munazajamil/Kali-Recon-Practice
So if you want to start learning ethical hacking start with free resources available on YouTube and read books. You can go short term diploma or you can also enroll in full time degree as well. Just start Learning and share you journey with me. If you found this guide useful. Keep an eye out for additional cyber security tutorials for beginners! Stay tuned with my blog for additional real life cyber security walkthroughs.
Just check out the cyber security roadmap for beginners. https://munazajameel.site/cybersecurity-roadmap-2025-beginners/. OR you can check out my YouTube channel for better content. https://www.youtube.com/@itzmunazah
See you next time!